User Account Control
DISCLAIMER! We make no claims or guarantees of this approach's security. If in doubt, enlist the help of an expert and conduct proper audits.
Making a viewer and its medical imaging data accessible on the open web can provide a lot of benefits, but requires additional security to make sure sensitive information can only be viewed by authorized individuals. Most image archives are equipped with basic security measures, but they are not robust/secure enough for the open web.
This guide covers one of many potential production setups that secure our sensitive data.
Overview#
This guide builds on top of our
Nginx + Image Archive guide,
wherein we used a reverse proxy
to retrieve resources from our image archive (Orthanc).
To add support for "User Account Control" we introduce
Keycloak. Keycloak is an open source
Identity and Access Management solution that makes it easy to secure
applications and services with little to no code. We improve upon our
reverse proxy setup by integrating Keycloak and Nginx to create an
authenticating reverse proxy.
An authenticating reverse proxy is a reverse proxy that only retrieves the resources on behalf of a client if the client has been authenticated. If a client is not authenticated they can be redirected to a login page.
This setup allows us to create a setup similar to the one pictured below:
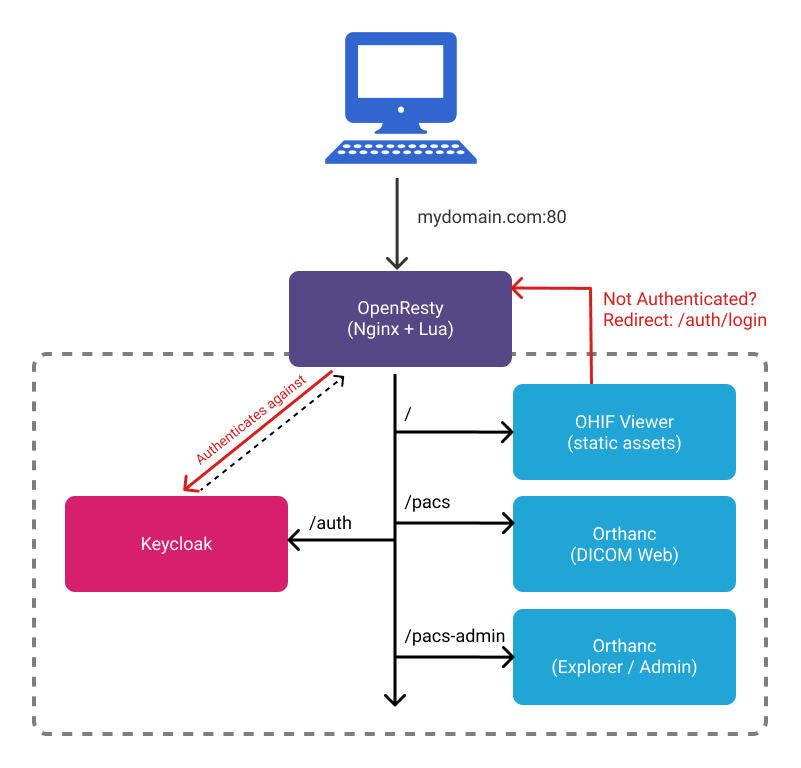
- All web requests are routed through
nginxon ourOpenRestyimage /pacsis a reverse proxy fororthanc'sDICOM Webendpoints- Requires valid
Authorization: Bearer <token>header
- Requires valid
/pacs-adminis a reverse proxy fororthanc's Web Admin/authis a reverse proxy forkeycloak- All static resources for OHIF Viewer are unprotected and accessible. We have
application logic that will redirect unauthenticated users to the appropriate
keycloaklogin screen.
Getting Started#
Requirements#
Not sure if you have docker installed already? Try running docker --version
in command prompt or terminal
Setup#
Spin Things Up
- Navigate to
<project-root>/docker/OpenResty-Orthanc-Keycloakin your shell - Run
docker-compose up
Create Your First User
- Navigate to:
http://127.0.0.1/auth/admin - Sign in with:
admin/password - From the top left dropdown, select the
Ohifrealm - From the left sidebar, under
Manage, selectUsers - Click
Add User- Username:
test - Email Verified:
ON - Click
Save
- Username:
- Click the
CredentialsTab- New Pasword:
test - Password Confirmation:
test - Temporary:
OFF - Click:
Reset Password
- New Pasword:
- From the top right dropdown, select
Admin, thenSign Out
Sign In
- Navigate to
http://127.0.0.1/ - Username:
test, Password:test - Click
Log In
Upload Your First Study
- Navigate to
http://127.0.0.1/pacs-admin - If you're not already logged in, use
test/test - From the top right, select "Upload"
- Click "Select files to upload..." (DICOM)
- Click "Start the upload"
- Navigate back to
http://127.0.0.1/to view your studies in the Study List
Troubleshooting#
Exit code 137
This means Docker ran out of memory. Open Docker Desktop, go to the advanced
tab, and increase the amount of Memory available.
Cannot create container for service X
Use this one with caution: docker system prune
X is already running
Stop running all containers:
- Win:
docker ps -a -q | ForEach { docker stop $_ } - Linux:
docker stop $(docker ps -a -q)
Configuration#
After verifying that everything runs with default configuration values, you will likely want to update:
- The domain:
http://127.0.0.1 - Set secure, non-default passwords
- Regenerate Keycloak Client Secrets
OHIF Viewer#
The OHIF Viewer's configuration is imported from a static .js file. The
configuration we use is set to a specific file when we build the viewer, and
determined by the env variable: APP_CONFIG. You can see where we set its value
in the dockerfile for this solution:
ENV APP_CONFIG=config/docker_openresty-orthanc-keycloak.js
You can find the configuration we're using here:
/public/config/docker_openresty-orthanc-keycloak.js
To rebuild the webapp image created by our dockerfile after updating the
Viewer's configuration, you can run:
docker-compose buildORdocker-compose up --build
Other#
All other files are found in: /docker/OpenResty-Orthanc-Keycloak/
| Service | Configuration | Docs |
|---|---|---|
| OHIF Viewer | dockerfile / config.js | You're reading them now! |
| OpenResty (Nginx) | /nginx.conf | lua-resty-openidc |
| Orthanc | /orthanc.json | Here |
| Keycloak | /ohif-keycloak-realm.json* |
* These are the seed values for Keycloak. They can be manually updated at
http://127.0.0.1/auth/admin
Keycloak Themeing#
The Login screen for the ohif-viewer client is using a Custom Keycloak
theme. You can find the source files for it in
/docker/OpenResty-Orthanc-Keycloak/volumes/keycloak-themes/. You can see how
we add it to Keycloak in the docker-compose file, and you can read up on how
to leverage custom themes in
Keycloak's own docs.
| Default Theme | OHIF Theme |
|---|---|
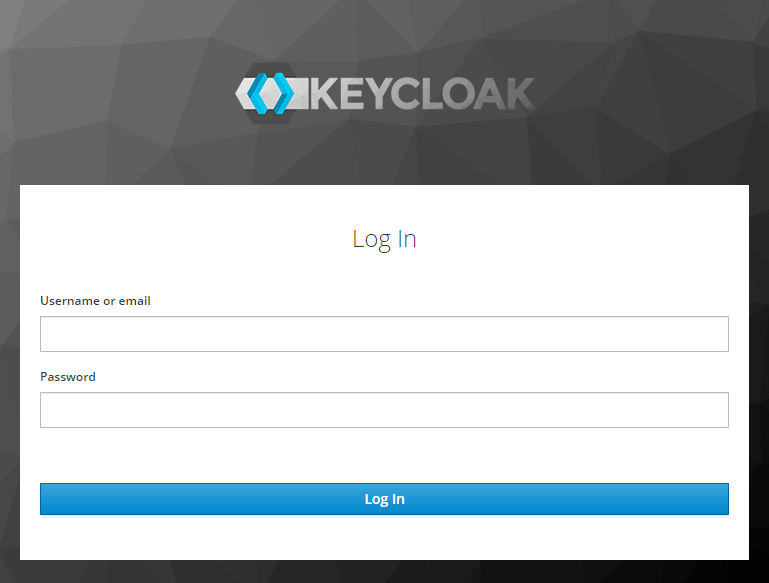 | 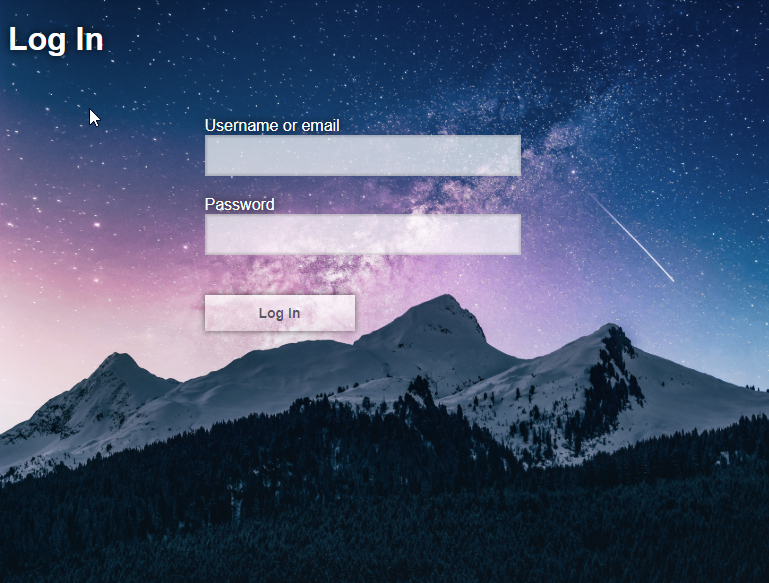 |
Next Steps#
Deploying to Production#
While these configuration and docker-compose files model an environment suitable for production, they are not easy to deploy "as is". You can either:
- Manually recreate this environment and deploy built application files OR
- Deploy to a cloud kubernetes provider like Digital Ocean OR
- Find and follow your preferred provider's guide on setting up swarms and stacks
Adding SSL#
Adding SSL registration and renewal for your domain with Let's Encrypt that terminates at Nginx is an incredibly important step toward securing your data. Here are some resources, specific to this setup, that may be helpful:
While we terminate SSL at Nginx, it may be worth using self signed certificates for communication between services.
Use PostgresSQL w/ Orthanc#
Orthanc can handle a large amount of data and requests, but if you find that
requests start to slow as you add more and more studies, you may want to
configure your Orthanc instance to use PostgresSQL. Instructions on how to do
that can be found in the
Orthanc Server Book, under
"PostgreSQL and Orthanc inside Docker"
Improving This Guide#
Here are some improvements this guide would benefit from, and that we would be more than happy to accept Pull Requests for:
- SSL Support
- Complete configuration with
.envfile (or something similar) - Keycloak Theme improvements
- Any security issues
- One-click deploy to a cloud provider
Resources#
Misc. Helpful Commands#
Check if nginx.conf is valid:
docker run --rm -t -a stdout --name my-openresty -v $PWD/config/:/usr/local/openresty/nginx/conf/:ro openresty/openresty:alpine-fat openresty -c /usr/local/openresty/nginx/conf/nginx.conf -tInteract w/ running container:
docker exec -it CONTAINER_NAME bash
List running containers:
docker ps
Clear Keycloak DB so you can re-seed values:
docker volume pruneORdocker volume lsanddocker volume rm VOLUME_NAME VOLUME_NAME
Referenced Articles#
The inspiration for our setup was driven largely by these articles:
- Securing Nginx with Keycloak
- Authenticating Reverse Proxy with Keycloak
- Securing APIs with Kong and Keycloak
For more documentation on the software we've chosen to use, you may find the following resources helpful:
We chose to use a generic OpenID Connect library on the client, but it's worth noting that Keycloak comes packaged with its own:
If you're not already drowning in links, here are some good security resources for OAuth:
For a different take on this setup, check out the repositories our community members put together: